Valentine’s Day 2026 isn’t just about flowers; it’s about Verification.
In the old days, “Catfishing” meant using a fake photo. Today, attackers are using Generative AI to clone voices in real-time. This isn’t just a dating problem; it is a massive Access Control problem for cybersecurity professionals.
The Threat: “Synthetic Media” vs. Biometrics
For the Security+ and CISSP exams, you need to understand why voice authentication is failing.
- The Technology: Tools like ElevenLabs can clone a voice with just 3 seconds of audio (often scraped from TikTok or Instagram).
- The Attack Vector: Attackers call victims pretending to be a “distressed boyfriend” or “kidnapped wife” to demand money (Vishing).
- The Enterprise Risk: Attackers use these clones to trick IT Help Desks into resetting passwords (“Deepfake CEO Fraud”).
Exam Concept: False Acceptance Rate (FAR)
We discussed this last month. AI Voice Clones dramatically increase the False Acceptance Rate (FAR) of voice biometric systems.
- Type II Error: The system thinks the AI is you.
- Mitigation: You cannot rely on “Something You Are” (Voice) alone anymore. You need MFA (Multi-Factor Authentication).
How to Protect Yourself (and Your Organization)
- The “Safe Word” Protocol: Agree on a secret word with your family/partner. AI can’t guess a secret shared offline. (This is a form of “Something You Know”).
- Hang Up and Call Back: If your “boss” calls asking for money, hang up and call their known internal number. This is Out-of-Band Authentication.
📱 Don’t Let a Deepfake Trick You
Identifying a synthetic voice is a skill you can learn.
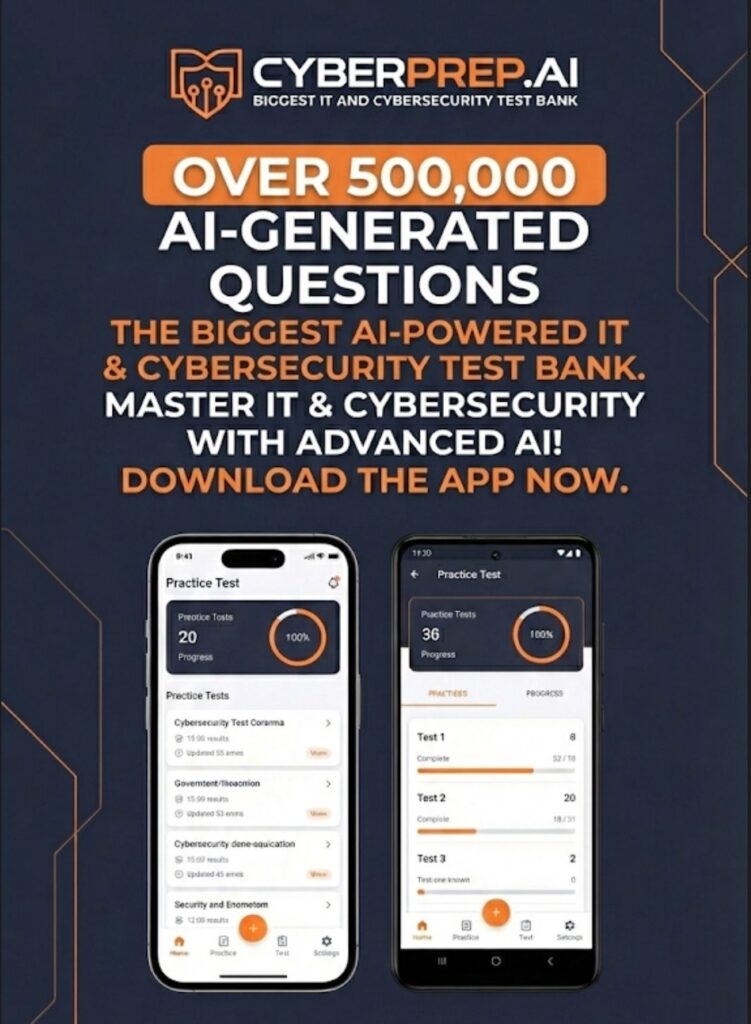
In the CyberPrep App, we have specific modules on Biometrics and Social Engineering attacks.
- Can you spot the difference between a Replay Attack and a Synthetic Voice?
- Do you know which biometric factor is the least secure?
Test your knowledge now:
🍏 Download on iOS App Store
🤖 Download on Google Play Store
Conclusion
Trust, but verify. Especially if “love” is asking for a wire transfer.