If you have looked at a job description or attended a security conference in 2025, you have heard the phrase “Zero Trust.”
It has become the industry’s favorite buzzword. Vendors try to sell it to you in a box. Managers throw it around in meetings. But for students studying for the CompTIA Security+ (SY0-701) or CISSP, Zero Trust isn’t just marketing fluff—it is the new standard of network security.
The days of the “Castle and Moat” are over. Here is what you need to know about the architecture of the future.
The Death of the “Castle and Moat”
Traditionally, network security worked like a medieval castle.
- The Moat: Firewalls and VPNs protected the perimeter.
- The Castle: Once you logged in (crossed the drawbridge), you were “trusted.” You could move around the network freely.
The Problem: If a hacker gets past the moat (via a phishing email or stolen password), they have free reign to move laterally and steal everything.
The New Reality: Never Trust, Always Verify
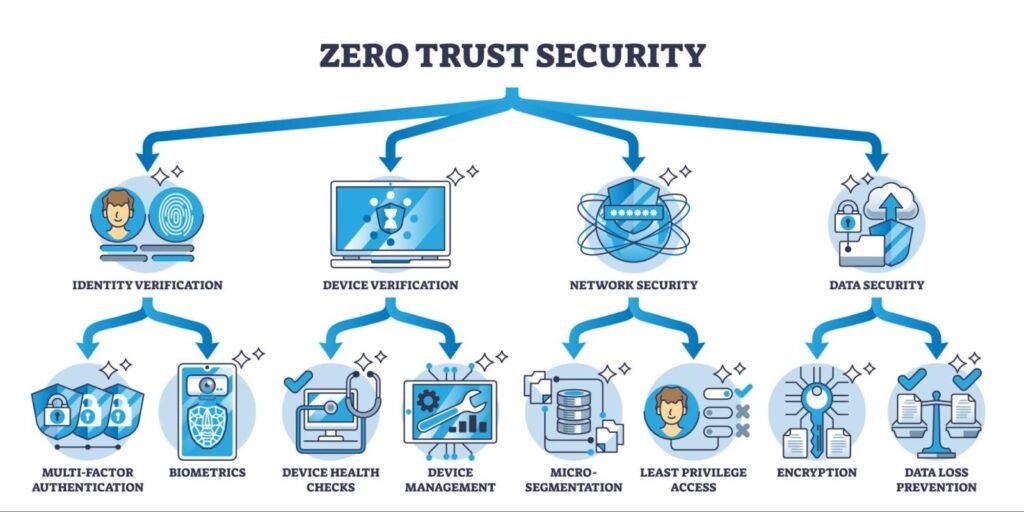
Zero Trust Architecture (ZTA) assumes that the network is already compromised. It operates on a simple, ruthless philosophy: Trust no one. Verify everyone.
It doesn’t matter if the login request comes from the CEO’s laptop inside the headquarters. The system treats it with the same suspicion as a request coming from a hacker in a coffee shop.
The 3 Pillars of Zero Trust (NIST 800-207)
For your exams, you need to understand the three core principles defined by NIST:
1. Verify Explicitly
Don’t just trust a password. Always authenticate and authorize based on all available data points.
- Is the user who they say they are? (MFA)
- Is the device healthy? (Patch levels, Antivirus status)
- Is the location weird? (Geolocation)
2. Use Least Privilege Access
Limit user access with Just-In-Time and Just-Enough-Access (JIT/JEA).
- Users should only have access to the specific file they need, right now.
- Once the task is done, access is revoked.
3. Assume Breach
Design your network as if an attacker is already inside.
- Micro-segmentation: Break the network into tiny, isolated zones. If a hacker breaches the “HR Zone,” they cannot jump to the “Finance Zone” because there is a firewall between them.
- Encryption: Encrypt all data, whether it is sitting on a hard drive (Rest) or moving across the cable (Transit).
📝 Exam Tip: Zero Trust on the SY0-701
The new Security+ exam (SY0-701) places a massive emphasis on Zero Trust compared to the old version.
You will see questions like:
“A company wants to implement a security model where location is not a factor for trust, and continuous verification is required for every resource request. Which model should they use?”
If you see “Continuous Verification” or “Micro-segmentation,” the answer is almost always Zero Trust.
Get Ready for 2026
Zero Trust isn’t going away. In 2026, it will likely be the default requirement for most enterprise security roles.
Don’t let the buzzwords intimidate you. At CyberPrep.ai, we have updated our test bank to include specific scenarios on Zero Trust implementation, Policy Enforcement Points (PEP), and Policy Decision Points (PDP).
Start the New Year ahead of the curve.